NEWS, EVENTS & BLOG
BLOG

What is a Trusted Platform Module (TPM)?
Press Office, VersaLogic Corporation, 01/06/21
The Best SBC for Secure Embedded Systems – Part 2
A few weeks ago, VersaLogic posted the first blog in the series “The Best SBC for Secure Embedded Systems”. That blog covered reasons for being concerned with security, provided an overview of the various types of security measures, and delved deeper into processor-based security measures. This month we’ll look at the hardware-based Trusted Platform Module (TPM).
Why is it needed?
As the number of edge connections and IoT deployments grow, so does the opportunity for hacking.
The internet has become a critical part of our everyday lives
TPM provides a hardware component that enables increased security when compared with software-only solutions. Without TPM, systems boot and then execute whatever code is on a drive, putting the system and any connected systems at risk. With TPM, the boot starts from a trusted source and each successive state is authenticated. Unauthorized code is not executed, regardless of how it found its way into the system.
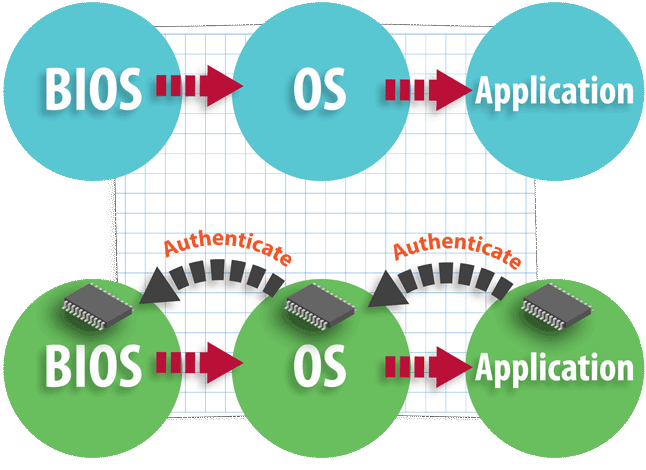
Risky, unauthenticated vs. TPM’s authenticated process
How is a Trusted Platform Module implemented?
There are three hardware means of implementing TPM and one software method. A software method may sound at odds with the concept of establishing a hardware root of trust. It is open to vulnerabilities; however, it is intended only as a software emulator for the building and testing of system prototypes (including TPM). The table below shows the attributes of the hardware implementation methods.
| TPM Type | Attributes |
| Discrete |
|
| Integrated |
|
| Firmware |
|
For critical applications, such as those in aerospace and defense, automotive control, and industrial automation, the discrete TPM type is most suitable. Firmware-based systems might be more suitable for applications such as an entertainment system.
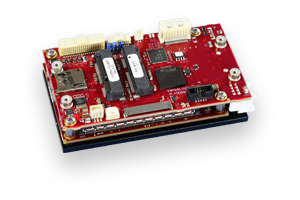
VersaLogic’s Harrier and Owl embedded computers are equipped with discrete TPM 2.0 protection
How does Trusted Platform Module Help?
There are several security issues that TPM is designed to solve:
| Security Issue | TPM contribution |
| Device Authentication | HW root of trust based on cryptographic keys securely stored in TPM |
| Secure communication | Integration with communications protocols such as OpenSSL |
| Data Security | Data encryption and securely stored cryptographic keys |
| Boot and Device Integrity | Trusted boot detects malware |
| Secure Updates | HW root of trust secures SW and FW updates |
Originally developed by the Trusted Computing Group, the TPM concept was standardized as ISO/IEC 11889 in 2009. TPM has progressed through a number of revisions with versions 1.1 and 1.2 being widely adopted and has now reached revision 2.0. This latest revision has been standardized as ISO/IEC11889:2015.
One of the enhancements of TPM 2.0 was to adopt a library approach. Users can choose from the various elements of TPM functionality depending of the security requirements of their application.
For more information on TPM 2.0, the Trusted Computing Group has an informative briefing document that contains links to other resources. Manufacturers of TPM devices such as Infineon are also another source of additional information.
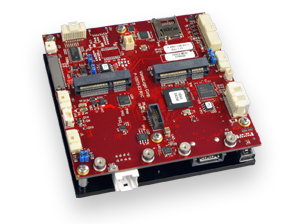
VersaLogic’s PC/104 Lion and Grizzly Embedded Server are equipped with discrete TPM 2.0 protection
That’s where we’ll leave the security story for now. Look out for the next piece in the security blog series covering remote access considerations and physical security.
Need additional Information?
Want to know more about VersaLogic’s range of products with TPM? Let’s start a conversation.